CyberArk Identity is a SaaS-delivered suite of solutions designed to simplify identity and access management in enterprises. CyberArk Identity unifies Workforce Access and Identity Management solutions in a single offering. Workforce Access capabilities include single sign-on, multi-factor authentication, session security, and credential management. Identity Management capabilities include lifecycle management, identity orchestration, and identity governance. With CyberArk Identity, organizations can secure workforce access to applications, endpoints, and infrastructure and protect themselves from the leading cause of data breaches – compromised credentials.
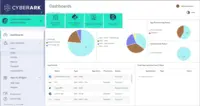
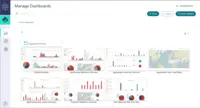
CyberArk Identity is part of the CyberArk Identity Security Platform. Built for the dynamic enterprise, CyberArk Identity Security Platform secures access for any identity to any resource or environment from anywhere using any device. The CyberArk Identity Security Platform enables operational efficiencies with a single admin portal, streamlines meeting compliance requirements with unified audit capabilities, and delivers Identity Security Intelligence for continuous identity threat detection and protection.
Workforce Access solutions:
CyberArk Single Sign-On (SSO) is a solution for one-click access to cloud, mobile, and legacy apps. CyberArk SSO enables a secure and frictionless sign-in experience for both internal and external users that adjusts based on risk.
CyberArk Secure Web Sessions is a cloud-based service that enables organizations to monitor, record, and audit end-user activity within high-risk and high-value web applications. Security and compliance specialists can use Secure Web Sessions to search recorded sessions using free text input and quickly filter events by users, dates, and actions.
Identity Management Services:
CyberArk Identity Lifecycle Management provides a way to route application access requests, create application accounts, manage entitlements for those accounts, and revoke access when necessary.
CyberArk Identity Flows is an identity orchestration solution that improves security, efficiency, and productivity by automating identity data and events. With Identity Flows, organizations can automate complex identity management workflows and synchronize identity data across diverse applications, directory stores, and repositories.
CyberArk Identity Compliance solution continuously discovers access, streamlines access certifications, and provides comprehensive identity analytics. Identity Compliance automates manually intensive, error-prone administrative processes, ensuring all workforce and privileged access rights are properly assigned and continually certified across enterprises.